Flipper Zero meets restaurants' pager systems (DDoS attack)
I'm not responsible for any usage outside this scope and I really discourage it.
On the other hand, it contains interesting information to keep in mind for restaurants' managers/owners while evaluating solutions like pagers.
Firstly, if you didn't read the above disclaimer, please read it and then go on.
Intro
Have you ever thought about what's under the hood of restaurants' pagers?


Well, I didn't either until I started playing with Flipper Zero in the last weeks.
User experience
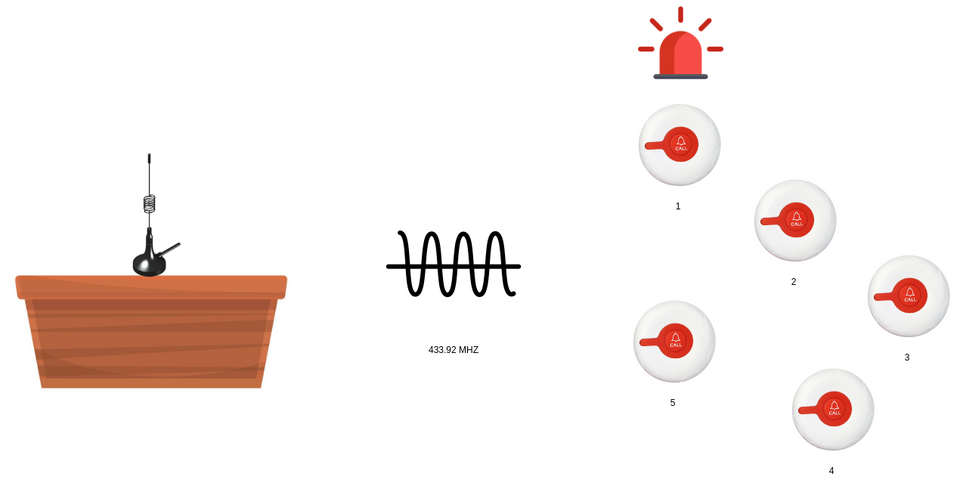
Basically, in some restaurants, they give you a pager after the order.
In this way, once ready, waiters instead of shout they can make the specific pager sound or vibrate, so the client is able to pick up her/his meal.
Technology under the hood
The technology under the hood is very simple.
The antenna, once the meal is ready, sends a packet on 433.92 MHZ frequency which will be received by receivers (pagers).
Each receiver will then emit a sound only if the packet is for itself, otherwise nothing happen.
Flipper Zero, is your turn!
Imagine being on the client side (on one of these kind of restaurants) and casually found a Flipper Zero on your pocket.
Well, in this case you can try to read some packets on 433.92MHZ frequency as below.
Since the protocol is known by Flipper Zero default firmware, you can use the "Read" functionality instead of "Read RAW" under the "Sub GHz" menu.
Wait a ready order and........ Flipper Zero will emit a small sound which indicate that it captured something.
After that, you are able to save it.
In order to analyze the content of the packets and understand better it, you can save more than one signal and take note of the pager number, which is usually a low number starting from 1.
Once saved, Flipper Zero allows to emulate it as many times you want.
⚠️⚠️⚠️ Keep in mind that you can cause a lot of problems to restaurants and make them losing time and of course money because you are making the pagers sound even if the meal is not ready. ⚠️⚠️⚠️
Anyway, the video below show the punctual emulation from Flipper Zero using a saved one.
Going deeper
Everything is nice, but we want to understand better what is the content of these packets on 433.92MHZ
It is enough to read the Flipper Zero SD card from a PC and under /subghz folder you will find all the caught signals during previous steps.
Here you can see an example of some packets of a restaurant's pager systems.
As you can see the protocol is "Princeton" which is recognized by Flipper Zero firmware, but the notable thing is that only the last part of the "Key" field is what changes between different pagers.
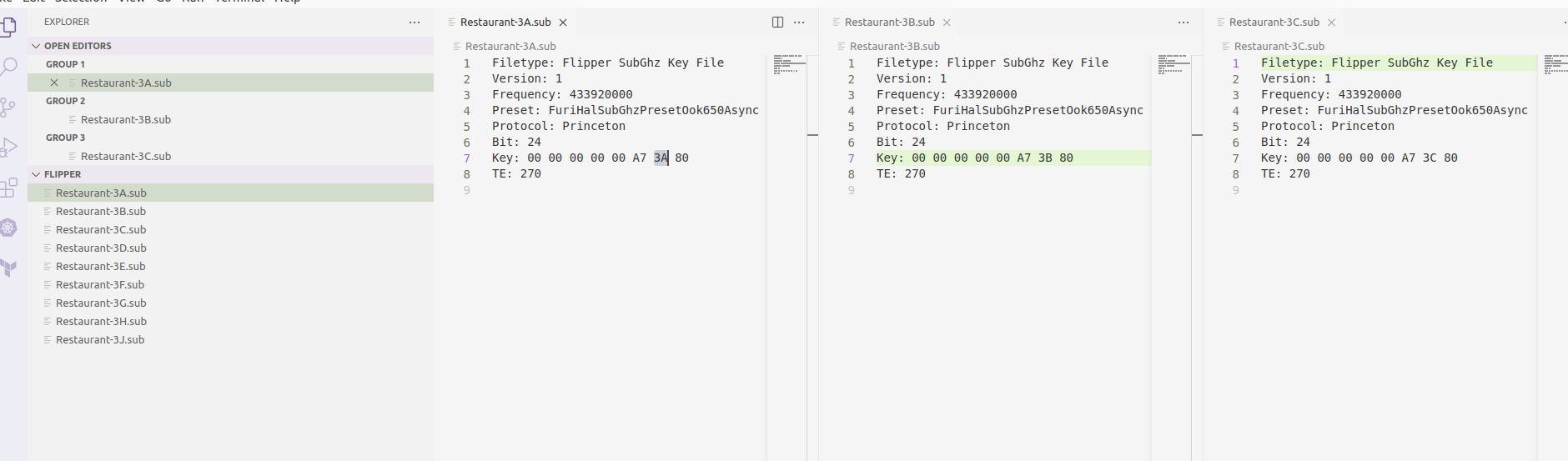
And this last thing is what make a specific pager sound instead of another.
Last but not least, editing these .sub files, you are able to create new saved sub-ghz signals with the "Key" you prefer.
Final considerations
This simple experiment allow understanding better what is under the hood of many restaurants' pagers system.
On the other hand, it highlights a potential vulnerability that can affect restaurants' owners/managers, since what we saw before could potentially be easily emulated at scale by criminals and literally block a restaurant.
The most common mitigation of this vulnerability is probably rolling code (code hopping) strategy.
More info here https://crypto.stackexchange.com/questions/18311/how-does-a-rolling-code-work
